Author Archives: admin2
Cryptocurrency: Pros and Cons for Investment
Learn what you need to know before you invest in a virtual currency
What Is Cryptocurrency?
A cryptocurrency is a digital or virtual currency that is secured by cryptography, which makes it nearly impossible to counterfeit or double-spend. Many cryptocurrencies are decentralized networks based on blockchain technology—a distributed ledger enforced by a disparate network of computers.
A defining feature of cryptocurrencies is that they are generally not issued by any central authority, rendering them theoretically immune to government interference or manipulation.
A cryptocurrency is a form of digital asset based on a network that is distributed across a large number of computers. This decentralized structure allows them to exist outside the control of governments and central authorities.
Some experts believe that blockchain and related technology will disrupt many industries, including finance and law.
The advantages of cryptocurrencies include cheaper and faster money transfers and decentralized systems that do not collapse at a single point of failure.
The disadvantages of cryptocurrencies include their price volatility, high energy consumption for mining activities, and use in criminal activities.
Understanding Cryptocurrencies
Cryptocurrencies are digital or virtual currencies underpinned by cryptographic systems. They enable secure online payments without the use of third-party intermediaries. “Crypto” refers to the various encryption algorithms and cryptographic techniques that safeguard these entries, such as elliptical curve encryption, public-private key pairs, and hashing functions.
Cryptocurrencies can be mined or purchased from cryptocurrency exchanges. Not all e-commerce sites allow purchases using cryptocurrencies. In fact, cryptocurrencies, even popular ones like Bitcoin, are hardly used for retail transactions. However, the skyrocketing value of cryptocurrencies has made them popular as trading instruments. To a limited extent, they are also used for cross-border transfers.
Blockchain
Central to the appeal and functionality of Bitcoin and other cryptocurrencies is blockchain technology. As its name indicates, blockchain is essentially a set of connected blocks or an online ledger. Each block contains a set of transactions that have been independently verified by each member of the network.
Every new block generated must be verified by each node before being confirmed, making it almost impossible to forge transaction histories.1 The contents of the online ledger must be agreed upon by the entire network of an individual node, or computer maintaining a copy of the ledger.
Experts say that blockchain technology can serve multiple industries, such as supply chains, and processes such as online voting and crowdfunding. Financial institutions such as JPMorgan Chase & Co. (JPM) are testing the use of blockchain technology to lower transaction costs by streamlining payment processing.
Types of Cryptocurrency
Bitcoin is the most popular and valuable cryptocurrency. An anonymous person called Satoshi Nakamoto invented it and introduced it to the world via a white paper in 2008. There are thousands of cryptocurrencies present in the market today.
Each cryptocurrency claims to have a different function and specification. For example, Ethereum’s ether markets itself as gas for the underlying smart contract platform. Ripple’s XRP is used by banks to facilitate transfers between different geographies.
Bitcoin, which was made available to the public in 2009, remains the most widely traded and covered cryptocurrency. As of May 2022, there were over 19 million bitcoins in circulation with a total market cap of around $576 billion. Only 21 million bitcoins will ever exist.
In the wake of Bitcoin’s success, many other cryptocurrencies, known as “altcoins,” have been launched. Some of these are clones or forks of Bitcoin, while others are new currencies that were built from scratch. They include Solana, Litecoin, Ethereum, Cardano, and EOS. By November 2021, the aggregate value of all the cryptocurrencies in existence had reached over $2.1 trillion—Bitcoin represented approximately 41% of that total value.4
Are Cryptocurrencies Legal?
Fiat currencies derive their authority from the government or monetary authorities. For example, each dollar bill is backstopped by the Federal Reserve.
But cryptocurrencies are not backed by any public or private entities. Therefore, it has been difficult to make a case for their legal status in different financial jurisdictions throughout the world. It doesn’t help matters that cryptocurrencies have largely functioned outside most existing financial infrastructure. The legal status of cryptocurrencies has implications for their use in daily transactions and trading. In June 2019, the Financial Action Task Force (FATF) recommended that wire transfers of cryptocurrencies should be subject to the requirements of its Travel Rule, which requires AML compliance.
As of May 2022, El Salvador and the Central African Republic were the only countries in the world to accept Bitcoin as legal tender for monetary transactions.6 In the rest of the world, cryptocurrency regulation varies by jurisdiction.
Japan’s Payment Services Act defines Bitcoin as legal property. Cryptocurrency exchanges operating in the country are subject to collect information about the customer and details relating to the wire transfer. China has banned cryptocurrency exchanges and mining within its borders. India was reported to be formulating a framework for cryptocurrencies in December.
Cryptocurrencies are legal in the European Union.
Derivatives and other products that use cryptocurrencies will need to qualify as “financial instruments.” In June 2021, the European Commission released the Markets in Crypto-Assets (MiCA) regulation that sets safeguards for regulation and establishes rules for companies or vendors providing financial services using cryptocurrencies.
Within the United States, the biggest and most sophisticated financial market in the world, crypto derivatives such as Bitcoin futures are available on the Chicago Mercantile Exchange. In the past, the Securities and Exchange Commission (SEC) took the stance that Bitcoin and Ethereum were not securities; however, in September 2022, SEC Chair Gary Gensler stated he believes cryptocurrencies are securities. This stance implies that cryptocurrency’s legal status may become subject to regulation.
Although cryptocurrencies are considered a form of money, the Internal Revenue Service (IRS) treats them as a financial asset or property. And, as with most other investments, if you reap capital gains in selling or trading cryptocurrencies, the government wants a piece of the profits. On May 20, 2021, the U.S. Department of the Treasury announced a proposal that would require taxpayers to report any cryptocurrency transaction of and above $10,000 to the IRS.11 How exactly the IRS would tax proceeds—as capital gains or ordinary income—depends on how long the taxpayer held the cryptocurrency.
Are Cryptocurrencies Safe Investments?
Cryptocurrencies have attracted a reputation as unstable investments, due to high investor losses as a result of scams, hacks, and bugs. Although the underlying cryptography is generally secure, the technical complexity of using and storing crypto assets can be a major hazard to new users.
In addition to the market risks associated with speculative assets, cryptocurrency investors should be aware of the following risks:
User risk: Unlike traditional finance, there is no way to reverse or cancel a cryptocurrency transaction after it has already been sent. By some estimates, about a fifth of all bitcoins are now inaccessible due to lost passwords or incorrect sending addresses.
Regulatory risks: The regulatory status of some cryptocurrencies is still unclear, with many governments seeking to regulate them as securities, currencies, or both. A sudden regulatory crackdown could make it difficult to sell cryptocurrencies, or cause a market-wide price drop.
Counterparty risks: Many investors and merchants rely on exchanges or other custodians to store their cryptocurrency. Theft or loss by one of these third parties could result in the loss of one’s entire investment.
Management risks: Due to the lack of coherent regulations, there are few protections against deceptive or unethical management practices. Many investors have lost large sums to management teams that failed to deliver a product.
Programming risks: Many investment and lending platforms use automated smart contracts to control the movement of user deposits. An investor using one of these platforms assumes the risk that a bug or exploit in these programs could cause them to lose their investment.
Market Manipulation: Market manipulation remains a substantial problem in the cryptocurrency space, and some exchanges have been accused of manipulating prices or trading against their customers.
Despite these risks, cryptocurrencies have seen a major leap in prices, with the total market capitalization rising to over $1 trillion.14 Despite the speculative nature of the asset, some have been able to create substantial fortunes by taking on the risk of investing in early-stage cryptocurrencies.
Advantages and Disadvantages of Cryptocurrency
Cryptocurrencies were introduced with the intent to revolutionize financial infrastructure. As with every revolution, however, there are tradeoffs involved. At the current stage of development for cryptocurrencies, there are many differences between the theoretical ideal of a decentralized system with cryptocurrencies and its practical implementation.
Some advantages and disadvantages of cryptocurrencies are as follows.
Advantages
Cryptocurrencies represent a new, decentralized paradigm for money. In this system, centralized intermediaries, such as banks and monetary institutions, are not necessary to enforce trust and police transactions between two parties. Thus, a system with cryptocurrencies eliminates the possibility of a single point of failure, such as a large bank, setting off a cascade of crises around the world, such as the one that was triggered in 2008 by the failure of institutions in the United States.
Cryptocurrencies promise to make it easier to transfer funds directly between two parties, without the need for a trusted third party like a bank or a credit card company. Such decentralized transfers are secured by the use of public keys and private keys and different forms of incentive systems, such as proof of work or proof of stake.
Because they do not use third-party intermediaries, cryptocurrency transfers between two transacting parties are faster as compared to standard money transfers. Flash loans in decentralized finance are a good example of such decentralized transfers. These loans, which are processed without backing collateral, can be executed within seconds and are used in trading.
Cryptocurrency investments can generate profits. Cryptocurrency markets have skyrocketed in value over the past decade, at one point reaching almost $2 trillion. As of May 2022, Bitcoin was valued at more than $550 billion in crypto markets.
The remittance economy is testing one of cryptocurrency’s most prominent use cases. Currently, cryptocurrencies such as Bitcoin serve as intermediate currencies to streamline money transfers across borders. Thus, a fiat currency is converted to Bitcoin (or another cryptocurrency), transferred across borders, and, subsequently, converted to the destination fiat currency. This method streamlines the money transfer process and makes it cheaper.
Disadvantages
Though they claim to be an anonymous form of transaction, cryptocurrencies are actually pseudonymous. They leave a digital trail that agencies such as the Federal Bureau of Investigation (FBI) can decipher. This opens up possibilities of governments or federal authorities tracking the financial transactions of ordinary citizens.18
Cryptocurrencies have become a popular tool with criminals for nefarious activities such as money laundering and illicit purchases. The case of Dread Pirate Roberts, who ran a marketplace to sell drugs on the dark web, is already well known. Cryptocurrencies have also become a favorite of hackers who use them for ransomware activities.19
In theory, cryptocurrencies are meant to be decentralized, their wealth distributed between many parties on a blockchain. In reality, ownership is highly concentrated. For example, an MIT study found that just 11,000 investors held roughly 45% of Bitcoin’s surging value.20
One of the conceits of cryptocurrencies is that anyone can mine them using a computer with an Internet connection. However, mining popular cryptocurrencies requires considerable energy, sometimes as much energy as entire countries consume. The expensive energy costs coupled with the unpredictability of mining have concentrated mining among large firms whose revenues running into the billions of dollars. According to an MIT study, 10% of miners account for 90% of its mining capacity.
Though cryptocurrency blockchains are highly secure, other crypto repositories, such as exchanges and wallets, can be hacked. Many cryptocurrency exchanges and wallets have been hacked over the years, sometimes resulting in millions of dollars worth of “coins” stolen.
Cryptocurrencies traded in public markets suffer from price volatility. Bitcoin has experienced rapid surges and crashes in its value, climbing to as high as $17,738 in December 2017 before dropping to $7,575 in the following months.3 Some economists thus consider cryptocurrencies to be a short-lived fad or speculative bubble.
How Do You Buy Cryptocurrencies?
Any investor can purchase cryptocurrency from popular crypto exchanges such as Coinbase, apps such as Cash App, or through brokers. Another popular way to invest in cryptocurrencies is through financial derivatives, such as CME’s Bitcoin futures, or through other instruments, such as Bitcoin trusts and Bitcoin ETFs.
What Is the Point of Cryptocurrency?
Cryptocurrencies are a new paradigm for money. Their promise is to streamline existing financial architecture to make it faster and cheaper. Their technology and architecture decentralize existing monetary systems and make it possible for transacting parties to exchange value and money independently of intermediary institutions such as banks.
Can You Generate Cryptocurrency?
Cryptocurrencies are generated by mining. For example, Bitcoin is generated using Bitcoin mining. The process involves downloading software that contains a partial or full history of transactions that have occurred in its network. Though anyone with a computer and an Internet connection can mine cryptocurrency, the energy- and resource-intensive nature of mining means that large firms dominate the industry.
What Are the Most Popular Cryptocurrencies?
Bitcoin is by far the most popular cryptocurrency followed by other cryptocurrencies such as Ethereum, Binance Coin, Solana, and Cardano.
Are Cryptocurrencies Securities?
In the past, the SEC has said that Bitcoin and Ethereum, the top two cryptocurrencies by market cap, were not securities. In September 2022, SEC Chair Gary Gensler stated he believes cryptocurrencies are securities and has asked SEC staff to begin working with crypto developers to register their crypto. However, he also clarified that he did not speak on behalf of the SEC; he was only speaking for himself. He encouraged those starting in the crypto space to register their crypto in the spirit of getting ahead because “It’s far less costly to do so from the outset.”
The Bottom Line
Cryptocurrencies are digital assets that are secured by cryptography. As a relatively new technology, they are highly speculative, and it is important to understand the risks involved before making an investment.
Investing in cryptocurrencies and other initial coin offerings (“ICOs”) is highly risky and speculative, and this article is not a recommendation by Investopedia or the writer to invest in cryptocurrencies or other ICOs. Because each individual’s situation is unique, a qualified professional should always be consulted before making any financial decisions. Investopedia makes no representations or warranties as to the accuracy or timeliness of the information contained herein.
“Services” added to menu …
Happy Iranian New Year 1395 – سال نو مبارک

Domain Name System (DNS)
The Domain Name System (DNS) is a hierarchical naming system built on a distributed database for computers, services, or any resource connected to the Internet or a private network. Most importantly, it translates domain names meaningful to humans into the numerical identifiers associated with networking equipment for the purpose of locating and addressing these devices worldwide.
An often-used analogy to explain the Domain Name System is that it serves as the phone book for the Internet by translating human-friendly computer hostnames into IP addresses. For example, the domain name www.example.com translates to the addresses 192.0.32.10 (IPv4) and 2620:0:2d0:200::10 (IPv6).
The Domain Name System makes it possible to assign domain names to groups of Internet resources and users in a meaningful way, independent of each entity’s physical location. Because of this, World Wide Web (WWW) hyperlinks and Internet contact information can remain consistent and constant even if the current Internet routing arrangements change or the participant uses a mobile device. Internet domain names are easier to remember than IP addresses such as 208.77.188.166 (IPv4) or 2001:db8:1f70::999:de8:7648:6e8 (IPv6). Users take advantage of this when they recite meaningful Uniform Resource Locators (URLs) and e-mail addresses without having to know how the computer actually locates them.
The Domain Name System distributes the responsibility of assigning domain names and mapping those names to IP addresses by designating authoritative name servers for each domain. Authoritative name servers are assigned to be responsible for their particular domains, and in turn can assign other authoritative name servers for their sub-domains. This mechanism has made the DNS distributed and fault tolerant and has helped avoid the need for a single central register to be continually consulted and updated.
In general, the Domain Name System also stores other types of information, such as the list of mail servers that accept email for a given Internet domain. By providing a worldwide, distributed keyword-based redirection service, the Domain Name System is an essential component of the functionality of the Internet.
Other identifiers such as RFID tags, UPCs, International characters in email addresses and host names, and a variety of other identifiers could all potentially use DNS.[1][2]
The Domain Name System also specifies the technical functionality of this database service. It defines the DNS protocol, a detailed definition of the data structures and communication exchanges used in DNS, as part of the Internet Protocol Suite.
شیوه جدید هک کردن حسابهای تلگرام در ایران
 امروزه بهخاطر استفاده روزافزون مردم در سراسر جهان، ازجمله ایرانیها، از اپلیکیشنهای موبایلی، فرصت مناسبی به هکرها داده تا بتوانند از این محبوبیت برای رخنه به حسابهای کاربران این ابزارها سوءاستفاده کنند. یکی از اپلیکیشنهای محبوب این روزها در ایران، اپلیکیشن پیامرسان «تلگرام» است. نزدیک به ۱۸ میلیون نفر بهصورت تقریبی از این «اپ» در ایران استفاده میکنند
امروزه بهخاطر استفاده روزافزون مردم در سراسر جهان، ازجمله ایرانیها، از اپلیکیشنهای موبایلی، فرصت مناسبی به هکرها داده تا بتوانند از این محبوبیت برای رخنه به حسابهای کاربران این ابزارها سوءاستفاده کنند. یکی از اپلیکیشنهای محبوب این روزها در ایران، اپلیکیشن پیامرسان «تلگرام» است. نزدیک به ۱۸ میلیون نفر بهصورت تقریبی از این «اپ» در ایران استفاده میکنند
یک حملهی هکری که چند روزیست بین کاربران شایع شده، این فرصت را در اختیار هکرها میگذارد تا با استفاده از جعل نام و تصویر تلگرام، طعمه را به دام انداخته و داخل حساب کاربری تلگرام فرد شوند
مراحلی که هکر انجام میدهد به این طریق است که، با یک نام جعلی و با تصویر لوگوی تلگرام برای شما پیامی همانند زیر ارسال میشود
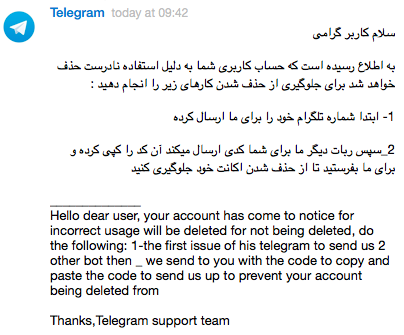
در نگاه اول، ممکن است به اشتباه متوجه شوید که این پیام را خود تلگرام ارسال کرده و وقتی نام کاربری را هم بررسی میکنید، اثری از نام کاربری و شماره تلفن وجود ندارد و شما ممکن است کمی بیشتر دچار اشتباه شوید اما درست فکر میکنید، این حساب کاربری تلگرام نیست. همانطور که در تصویر فوق قابل مشاهده است، هکر از شما درخواست شماره تلفن کرده است. بعد از این مرحله، هکر با وارد کردن شماره تلفن در سایت یا اپلیکلیشن تلگرام، خود را به عنوان کاربری جدید(با شماره شما) به سایت معرفی کرده و کد تائید از سوی تلگرام، از طریق پیامک یا پیام در داخل اپلیکیشن تلگرام برای شما ارسال میشود
برای امتحان این موضوع کد اشتباهی در اختیار هکر گذاشته شده و همانطور که در تصویر پایین قابل مشاهده است، هکر بار دیگر درخواست کد صحیح کرده است. اگر کد واقعی در اختیار هکر قرار میگرفت، او میتوانست به حساب دسترسی پیدا کند
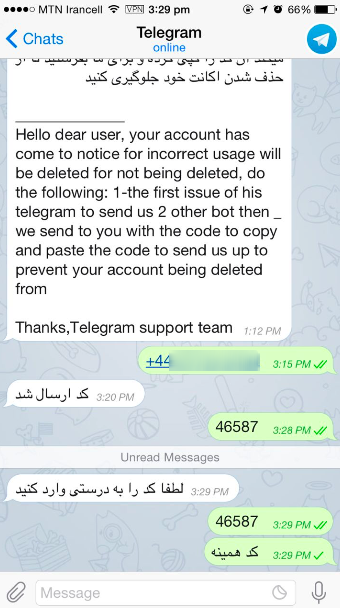
Source: Manoto1 website
Domain and Environment!
Do you need to advertise your business, product or …? printed one?!
Do you know how much paper will be wasted for that?! Unfortunately, in everyday life, we can see lots lots of advertising papers around us! What about our environment?!
There is a need to conserve our environment. Paper industry is a one of the largest users of wood for which trees are cut, leading to destructive effect on the environment.
Technology has come to help! Online technology is developed and capable of handling almost all kinds of transaction related to companies, organizations, colleges, institutes etc …
In spite of technology offering an environment friendly alternative, the use of paper has not reduced except in some countries.
We easily help you to start your domain and website in order to stop using paper, and start using e-paper! unlimited pages! and it can send your message more extend in almost all countries! Join us! Have a domain, Have a green world 🙂

Domains for sale
دامین های (دامنه های) زیر به فروش میرسند، در صورتی که علاقمند هستید، لطفا با info تماس بگیرید
These domains are for sale:
If you are interested in buying one of these, please send an email to info of Netbaran! (Apologize us that for avoiding spams we have to write email like this!)
How to protect your computer ?
How to protect your computer from hackers, spyware and viruses
These recommendations are very simple rules which should be observed. I will try to add more and give you details soon.
When a computer is attacked by a virus or hacker, first it’s the owners fault! So be sure you observe all these rules:
- Install Anti-Virus Software: and set it on auto-update or do it at least once in a week. Which kind of Antivirus?! Most of are effective, but the important thing is how to setup it ! if you don’t know how to set up an anti-virus, let us know.
- Update Windows and all Softwares: The most important software to keep up to date is your Windows operating system. It is essential to have Automatic Updates turned on and set to download and install updates automatically.
- Install only Trusted Softwares: Sometimes programs will ask you to install other programs during the install of the first application. Be careful of that because it’s usually a spyware. Install software from famous names only.
- Avoid P2P File Sharing Software: Avoid using P2P softwares which usually let you download music, movie and picture. Most of them are illegal and they may use your pc as an upload center and send spyware to your pc, So don’t use them if you are not a professional.
- Run Virus Scans Regularly: If you’re not in the mood to scan every day, at least run a scan once a week. Actually, setup a schedule for your computer in your anti-virus software to run a scan late at night or whenever you don’t use your computer and that way you won’t be bothered with a slow computer.
- Be careful what you attach to your computer: This is a more common way to transfer viruses than you might think. Everyone now has a USB flash disk that they carry around on their key chains, ready to snap into any computer. But who knows what your viruses are on your friends computers and what accidentally got transferred to their USB disk. A lot of virus programs will auto launch right when the USB disk is put into the computer, so you don’t even have to open or download any of the files to be infected.
- Avoid Shady Web Sites: Never go to illegal websites such as porn and …, You are DEFINITELY will have some viruses or spywares if you browse these sites.
- Turn on windows firewall: If you’re running Windows XP, make sure Windows Firewall is turned on. A firewall prevents hackers from gaining access to your computer by limiting the number of ports that are open to the public. Also, when buying a wireless router, make sure it has a built in firewall.
- Use a Complex Password for Login: This means that you should already have a password to login to your computer. Not having a password at all is not a good idea. Create a password for all user accounts and make sure it’s complex. Complex means it should have numbers, upper case characters, lower case characters, and symbols. This makes it way more difficult for a hacker to get into your computer.